With the holidays just around the corner, we need to be hyper-vigilant about spoofing and phishing attacks.
Over the past 24 months, spoofing and phishing attacks have become the most common attack vectors used by cybercriminals. So, for this month we want to provide a Spoofing & Phishing Refresher for our readers and provide some ways that you can avoid becoming a victim of these malicious and potentially life altering acts.
HOW SPOOFING AND PHISHING WORK TOGETHER
Spoofing is a technique deployed by cyber criminals to modify a domain name, phone number, email address, or IP address, and use it for unlawful purposes. Email is by far the most widely used form of spoofing. The objective of spoofing emails is to trick a user into thinking the email they are receiving is from a legitimate source and coerce them into taking some form of action.
When a victim is tricked into believing the email they are receiving is legitimate (successfully spoofed), they will be directed to click on a link or open an attachment. Once they click the link or carry out the request, they can become infected with malware, ransomware, or have their credentials hijacked. This is the act of phishing.
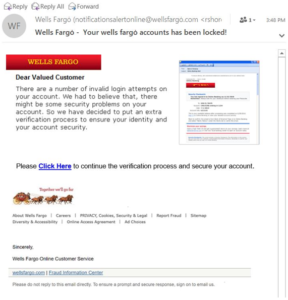 REAL LIFE SPOOFING AND PHISHING
REAL LIFE SPOOFING AND PHISHING
I received this email from Wells Fargo. The email address displayed is Wells Fargo (notificationsalertonline@wellsfargo.com). If you look closely at the word Wells Fargo in the email, there is a small dot positioned over the “o”. At a glance, the untrained eye may see this as a legitimate email. This is an obvious attempt to spoof me into clicking the “Click Here” link.
Clicking that link would most likely take me to a site that would ask for my username and password or I could be infected at that moment with malware or ransomware. This is a classic form of a successful phishing attack.
A best practice when viewing emails is to hover your mouse over the URL. This will reveal the actual URL where the email was generated.
Due to the lack of knowledge and training among the general population, cyber criminals are having tremendous success with these types of spoofing and phishing attacks. The damage they cause to people and organizations can be catastrophic!
 FACTS ABOUT SPOOFING AND PHISHING ATTACKS:
FACTS ABOUT SPOOFING AND PHISHING ATTACKS:
- Spoofing and phishing attempts have grown 65% in the last year
- 76% of businesses reported being a victim of a phishing attack in the last year
- 30% of spoofing messages get opened by targeted users and 12% of those users click on the malicious attachment or link
- 95% of all attacks on enterprise networks are the result of successful spear phishing
- 1.5 million new phishing sites are created each month
HOW TO COMBAT THE SPOOFING & PHISHING EPIDEMIC
The most effective way to reduce the threat of becoming a victim of spoofing and phishing attacks is by implementing a phishing simulation tool and security awareness training. A phishing simulation tool sends test phishing emails to see how vulnerable you are to spoofing and phishing attacks. They are designed to keep us alert and simulates different environments at which an attack could happen. Over time, organizations have seen up to a 90% decrease in successful spoofing and phishing attacks.
There are several companies in the market that offer these types of services. They are very cost effective and offered as a subscription-based service. There are also open source phishing tools that can be administered for free. Gartner Peer Insights is a great source for reviewing Phishing Simulation and Training programs. We listed the URL in the Sources below.
The cybercriminal landscape is only increasing as we get further into the Digital Age. The key is to look for a program that can assess, educate, measure, and reinforce good cyber hygiene. Until next month, wishing you a blessed Thanksgiving and safe travels in cyberspace!
Questions? Send me a tweet: @GoldSkyRon or email ron.frechette@goldskysecurity.com



